Key Features
- Flexible Controls: Allow, block, challenge, or log traffic based on IPs, CIDRs, ASNs, or entire countries.
- Curated Threat Lists: Continuously updated feeds from leading reputation sources, available on Advanced, Business, and Enterprise plans.
- Custom Lists: Create your own access policies with rules tailored to your exact needs, from trusted networks to high-risk regions.
- Instant Enforcement: Rules propagate globally within seconds and are applied directly at the edge without adding latency or backend complexity.
Multi-layer Access Control
Access Lists combine curated intelligence with your own rules to deliver adaptive protection:- Curated threat feeds cover VPNs, Tor nodes, abusive datacenters, and active attack sources.
- Custom rules allow you to define access logic for IPs, CIDRs, ASNs, or countries.
- ASN-based filtering gives you broad control over provider networks to stop botnets hiding behind hosting providers.
- Country-level rules make it easy to allow or block entire regions.
Access List Modes
Each Access List rule gives you full control over how Bunny Shield should handle matched traffic:- Allow: Ensure trusted traffic passes through without restriction.
- Block: Drop malicious requests at the edge instantly.
- Challenge: Trigger browser verification for suspicious traffic without blocking it outright.
- Log: Record traffic patterns for analysis without applying enforcement.
Action Precedence
When multiple rules apply to the same request, Bunny Shield follows a defined order of precedence to ensure consistent results:- Bypass: Always takes priority. Requests that match a Bypass skip further evaluation from Bunny Shield.
- Allow: Trusted traffic is passed through without restriction.
- Block: Requests are denied immediately if they match a block rule.
- Challenge: Suspicious requests are challenged if no higher-priority action applies.
- Log: If no other action matches, requests can be logged for monitoring and analysis.
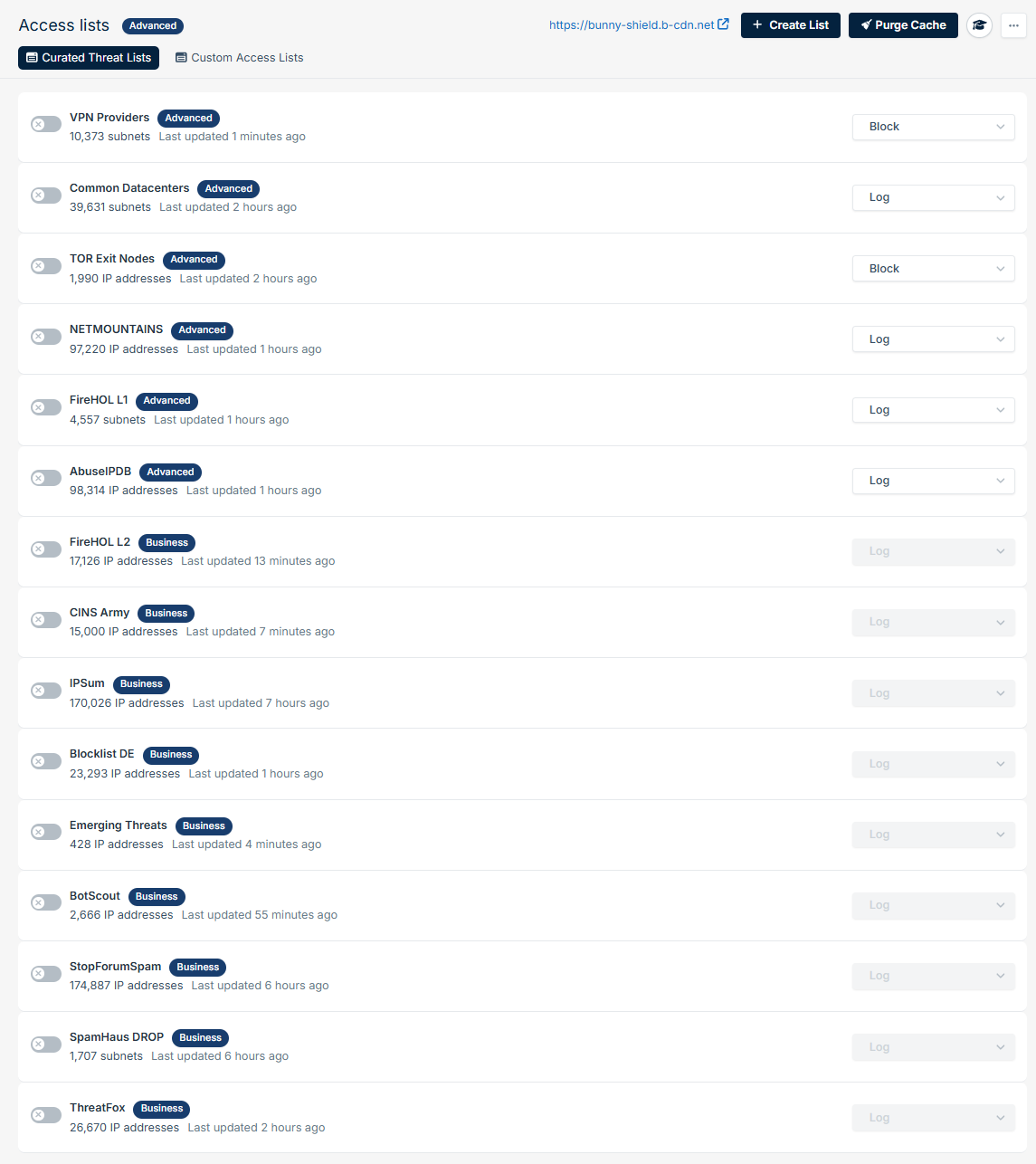
Curated Threat Intelligence
Bunny Shield maintains a library of continuously updated reputation feeds that are deployed instantly across the edge. These feeds protect against evolving threats without manual upkeep:- Advanced: VPNs, common datacenters, Tor exit nodes, FireHOL Level 1, AbuseIPDB, NetMountains
- Business: Includes all Advanced feeds plus Blocklist DE, ThreatFox, StopForumSpam, SpamHaus DROP, and more
- Enterprise: Includes all Advanced and Business feeds with support for custom feed integrations tailored to your infrastructure
Custom Access Lists
Custom Access Lists give you complete control over your traffic:- Allow internal ASNs or office IP ranges
- Block abusive regions during sensitive launches
- Challenge suspicious networks while monitoring behavior
- Apply unique lists to different zones or endpoints
Logging and Observability
Access Lists provide visibility into every decision, so you always know what is being allowed, blocked, or challenged:- Logged events: Requests matched by access rules without being blocked
- Actioned events: Requests that were blocked or challenged
- Curated feed hits: Requests flagged by built-in reputation lists